Following several other US states, and many legal jurisdictions around the world, Washington, D.C. has strengthened one of its key privacy laws: the Washington D.C. Data Breach Notification Law.
The Security Breach Protection Amendment Act of 2019, B23-0215, makes several important changes to the D.C. data breach law, including a broader definition of personal information, new data security obligations, and some new exceptions and exemptions for certain businesses.
The law applies to anyone doing business in Washington, D.C., who owns or licenses D.C. residents' personal information, whether established in the state or not. It's important to understand what these changes mean for your business.
There are two main reasons why you need a Privacy Policy:
✓ Privacy Policies are legally required. A Privacy Policy is required by global privacy laws if you collect or use personal information.
✓ Consumers expect to see them: Place your Privacy Policy link in your website footer, and anywhere else where you request personal information.
Generate an up-to-date 2024 Privacy Policy for your business website and mobile app with our Privacy Policy Generator.
One of our many testimonials:
"I needed an updated Privacy Policy for my website with GDPR coming up. I didn't want to try and write one myself, so TermsFeed was really helpful. I figured it was worth the cost for me, even though I'm a small fry and don't have a big business. Thanks for making it easy."
Stephanie P. generated a Privacy Policy
- 1. Broader Definition of Personal Information
- 2. New Requirements: Data Security
- 2.1. Reasonable Security Safeguards
- 2.2. Service Provider Contracts
- 2.3. Data Disposal
- 3. Breach Notifications
- 3.1. Definition of a Data Breach
- 3.2. New Exception: Low Risk of Harm
- 3.3. Existing Requirement: Notify the Affected Individuals
- 3.4. Existing Requirement: Notify Consumer Reporting Agencies
- 3.5. New Requirement: Notify the Attorney General
- 4. New Exemptions
- 5. New Requirement: ID Theft Services
- 6. Summary
Broader Definition of Personal Information
Arguably the most important change to the law is the expansion of the definition of "personal information."
Previously, the law limited the definition of "personal information" to a relatively narrow list of identifiers, including financial account information, names, addresses, etc. The amendment introduces many new identifiers, including an individual's email address and biometric data.
There are two reasons why this is such a significant change:
- It means that more companies will need to comply with the law.
- It means that covered businesses are more likely to need to report a breach.
There are two types of personal information under the Washington D.C. Breach Notification Law.
The first type of personal information consists of a combination of at least two components. One of the components must be an individual's:
- First name
- First initial and last name, or
- Any other personal identifier
The above component must be combined with any of the "data elements" below, provided that the personal identifier and the data element combined can be used to identify a person or the person's information.
-
ID numbers:
- Social security number
- Individual Taxpayer Identification Number
- Passport number
- Driver's license number
- District of Columbia identification card number
- Military identification number
- Another unique identification number issued on a government document commonly used to verify the identity of a specific individual
-
Payment details:
- Account number
- Credit card number
- Debit card number
-
Any other number or code, or combination of numbers or codes, that allows access to or use of an individual's financial or credit account, such as:
- Identification number
- Security code
- Access code
- Password
- Medical information
- Genetic information and deoxyribonucleic acid (DNA) profile
-
Health insurance information:
- Policy number
- Subscriber information number
- Any unique identifier used by a health insurer to identify the person that permits access to an individual's health and billing information
-
Biometric data (data about an individual that is generated by automatic measurements of their biological characteristics) that is used to uniquely authenticate the individual:
- Fingerprint
- Voiceprint
- Genetic print
- Retina or iris image
- Another unique biological characteristic
- Any combination of data elements I through VI above that would enable a person to commit identity theft without reference to a person's first name or first initial and last name or another independent personal identifier
The upshot of this is that you will not have suffered a data breach if an attacker accesses a list of names or a list of account numbers. You will have suffered a data breach if the attacker accesses a list of names and a corresponding list of account numbers.
The second type of personal information consists of a username or email address, in combination with one or more of the following:
- Password
- Security question and answer
- Another means of authentication
- Any combination of data elements I through VI above that permits access to an individual's email account
We recommend you conduct an audit of all the data your company holds and identify whether any of it qualifies as "personal information" under the law.
New Requirements: Data Security

Another significant change to the law is that covered businesses are required to implement data security measures. This requirement's scope is similar to that introduced under the California Consumer Privacy Act (CCPA).
Reasonable Security Safeguards
Businesses are required to maintain "reasonable security safeguards" to protect personal information.
Here's the relevant part of the law, at Section 28-3852.01 (a):
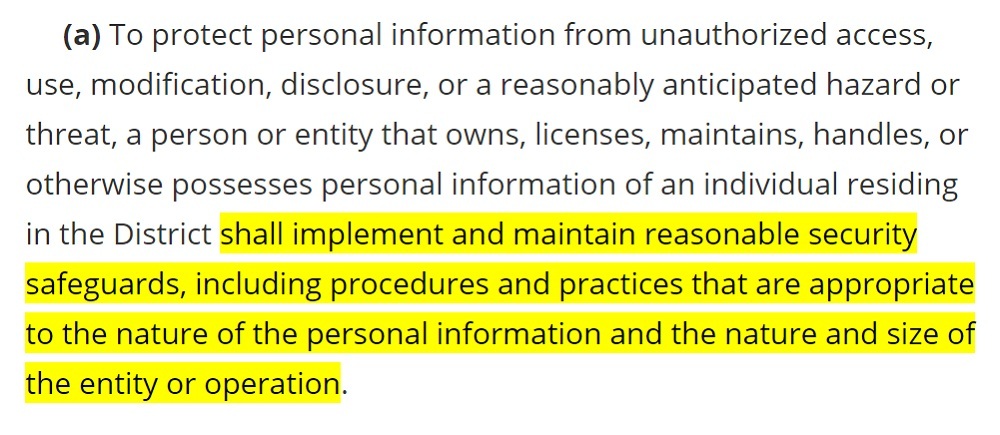
Your security safeguards must be appropriate to:
- The nature of the personal information. Consider how much harm might be caused if the personal information you hold was breached. Harm can be caused to a person's finances, reputation, or privacy.
- The nature and size of the entity or operation. Affordability can be a factor when determining which safeguards you implement. A higher standard of security will be expected from a larger company.
What constitutes a "reasonable" level of security is ultimately a matter for the courts. The Center for Internet Security (CIS) has a list of 20 controls that are a good starting point.
Service Provider Contracts
The law now requires businesses to ensure that personal information remains secure when they transfer it to a third party.
Suppose you transfer personal information to a service provider who processes the personal information on your behalf. In that case, you'll need to ensure that the service provider also implements reasonable security safeguards to protect the personal information.
There is a similar but more demanding provision under the CCPA. For more information about working with service providers under the CCPA, see our article The Complete Guide to CCPA Service Providers.
Here's the relevant part of the law at Section 28-3852.01 (b):

Complying with this step should amount to inserting a clause into your agreements with any service providers who have access to personal information. The clause should warrant the service provider to meet the requirements listed above.
Data Disposal
The law also requires covered businesses to take reasonable steps to protect personal information when destroying it.
Here's the relevant part of the law at Section 28-3852.01 (c):

Again, there is some discretion here as to the extent of the safeguards. You may consider affordability, and the disposal technology that is available.
Some methods of destroying electronic records include:
- Data wiping software
- Degaussing: Using magnetic fields to permanently erase data from physical media
- Disassembly
Breach Notifications
Definition of a Data Breach
The law defines a "breach of the security of the system" (data breach) at Section 28-3851 (1)(A):
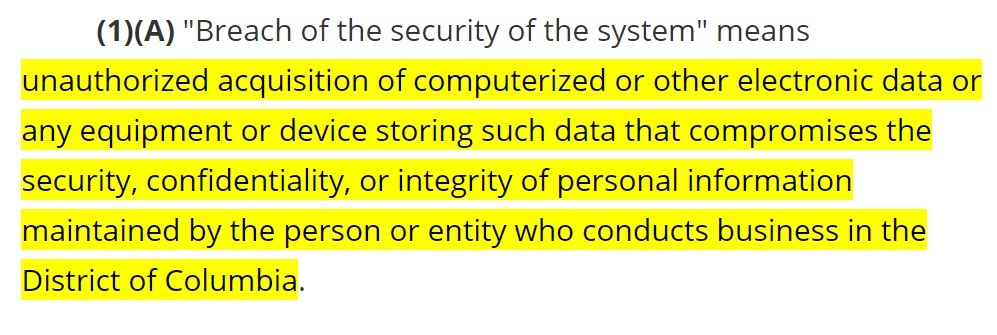
Any unauthorized access to personal information can qualify as a breach, whether:
- Intentional, e.g. via a cyberattack or data exfiltration
- Unintentional, e.g. via an email sent to the wrong recipient
- External, e.g. conducted by a hacker or phishing scam
- Internal, e.g. conducted by a trusted employee
The Act lists several exceptions to the definition of "data breach." These are types of unauthorized access that do not qualify as a data breach. The existing exceptions under the Act include:
- Where an employee or agent accesses personal information in good faith and does not misuse or disclose it
- Where the personal information is secure, for example, because it has been encrypted or redacted unless the encryption key has been compromised
New Exception: Low Risk of Harm
Under the amendments to the law, there is an additional exception to the definition of "data breach."
Unauthorized access to personal information will not qualify as a data breach if it is unlikely to cause harm to the affected individual. Here's the relevant part of the law, at Section 28-3851 (1)(B) iii:
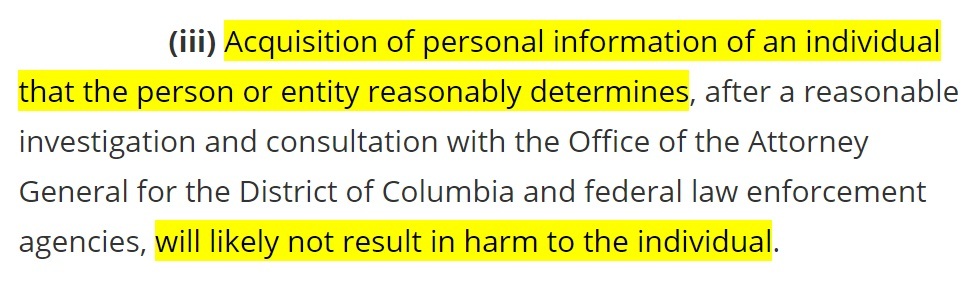
Note that the Attorney General must be involved in determining whether unauthorized access to personal information carries a risk of harm. Therefore, you must still report any potential data breach to the Attorney General.
Existing Requirement: Notify the Affected Individuals
The main purpose of the law is to require businesses to notify individuals if they have been subject to a data breach. Here's the relevant part of the law, at Section 28-3852 (a):
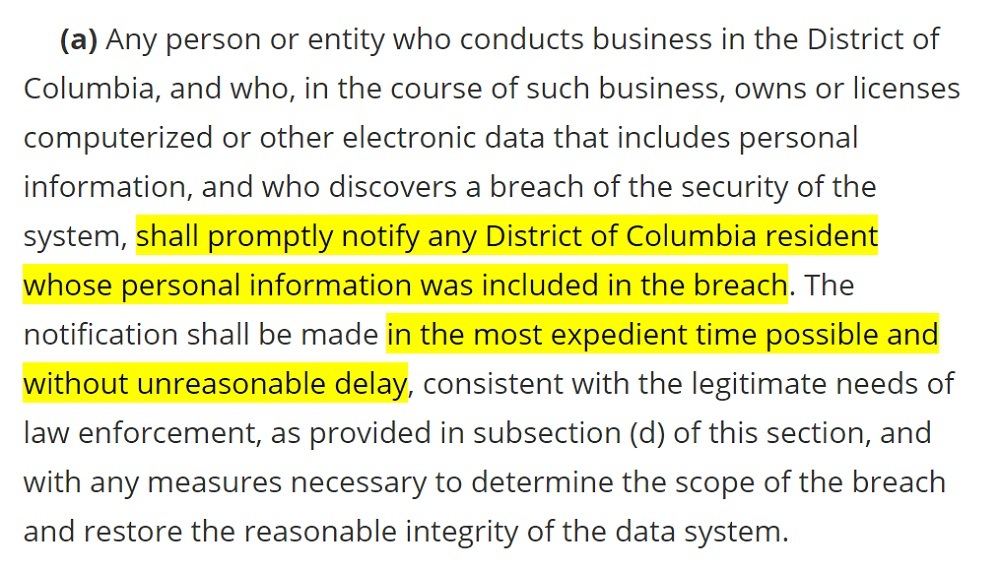
When contacting a D.C. resident, you must provide the following information:
- A description of the categories of information that were, or are reasonably believed to have been, acquired, including the elements of personal information that were, or are reasonably believed to have been, acquired.
-
Contact information, including your:
- Business address
- Phone number
- Toll-free number (if you have one)
- The toll-free telephone numbers and addresses for major consumer reporting agencies, plus information about how to obtain a free "security freeze" under the Fair and Accurate Credit Transactions Act (15 USC Section 1681 c-1 available, here).
-
The toll-free numbers, addresses, and websites for the following agencies, plus a statement that they offer identity theft advice:
- The Federal Trade Commission, and
- The Office of the Attorney General for the District of Columbia
You must notify affected individuals "in the most expedient time possible and without unreasonable delay." The only exception is where law enforcement requires you to delay notification, seen here at Section 28-3852 (d):
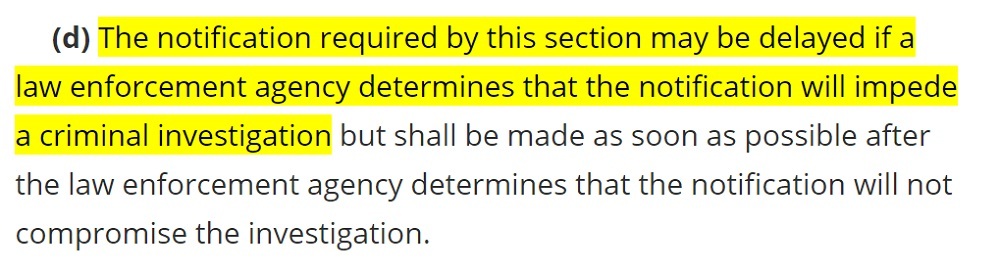
Existing Requirement: Notify Consumer Reporting Agencies
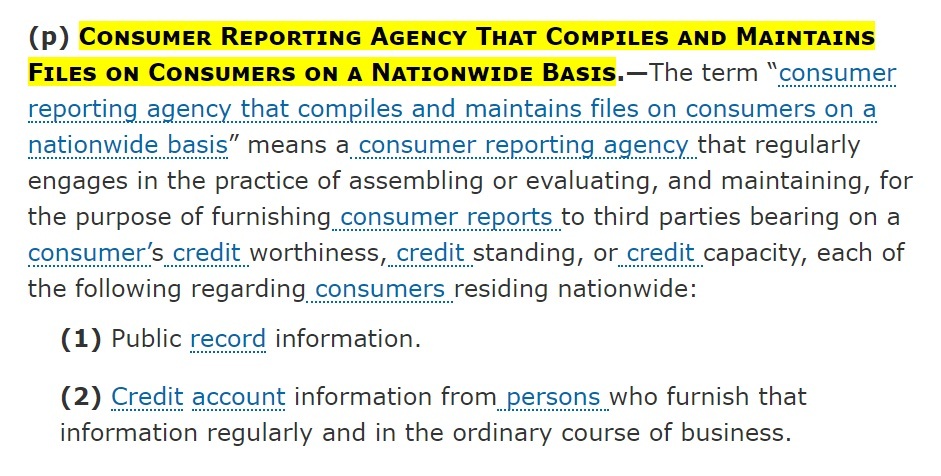
Where over 1000 D.C. residents are affected by a data breach, you must also notify consumer reporting agencies:

The Act takes its definition of a "consumer reporting agency" from the Fair Credit Reporting Act (15 U.S.C. Section 1681a (p), available here):
New Requirement: Notify the Attorney General
In addition to the original requirement to notify affected individuals in the event of a data breach, the Act now requires businesses to notify the D.C. Attorney General if the breach affects 50 or more D.C. residents at Section 28-3852 (b-1):
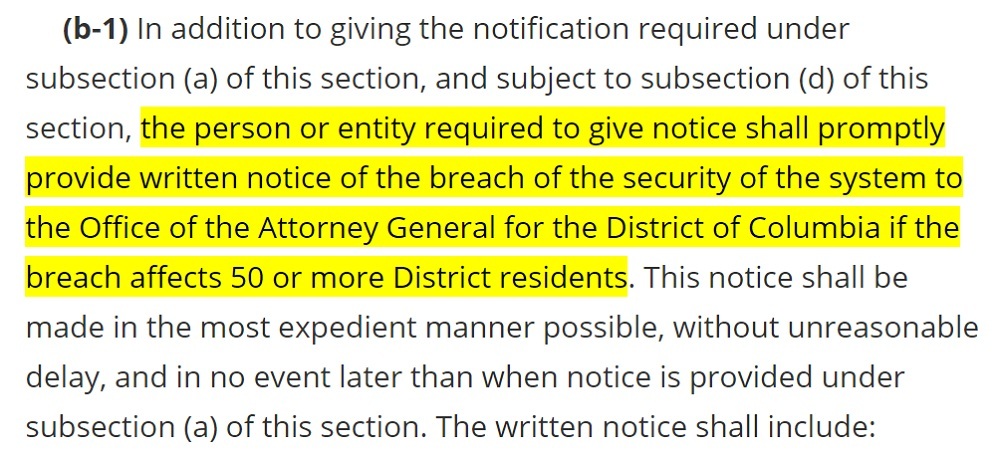
Note that if you aren't sure whether 50 D.C. residents have been affected, you must still notify the Attorney General. The Act states that you must not delay until you have ascertained how many D.C. residents have been affected.
When notifying the Attorney General, you must provide the following information:
- The name and contact information of the person or entity reporting the breach
- The name and contact information of the person or entity that experienced the breach
- The nature of the breach, including the name of the person or entity that experienced the breach
- The types of personal information compromised
- The number of D.C. residents affected
- The cause of the breach, including the relationship between the person or entity that experienced the breach and the person responsible for the breach, if known
- The remedial action that has been taken by the affected person or entity, including the steps taken to assist affected D.C. residents
- The date and time frame of the breach, if known
- The address and location of your headquarters, if outside of D.C.
- Whether a foreign country was involved in the breach
- A sample of the notice to be provided to D.C. residents
New Exemptions

Organizations subject to the Health Insurance Portability and Accountability Act (HIPAA) or the Gramm-Leach-Bliley Act (GLBA) are no longer required to comply with the Washington D.C. Data Breach Notification Law.
These exemptions are on the proviso that the organization is fully compliant with one of these laws. The exemption recognizes that the breach notification process under these laws is as rigorous as that required by the D.C. Act.
Where an organization experiences a data breach that requires notification under HIPAA or the GBLA, it will still need to notify the D.C. Attorney General if D.C. residents have been affected.
New Requirement: ID Theft Services
If you suffer a data breach that results in unauthorized access to a D.C. resident's social security number or tax ID number, you must offer that resident identity theft services for a period of at least 18 months.
Summary
The changes to the Washington D.C. Breach Notification Law brings it in-line with some of the stricter privacy laws across the United States.
The new provisions of the law include:
- A broader definition of "personal information"
- A new obligation to keep personal information secure
- A new requirement to ensure service providers keep personal information secure
- A new requirement to dispose of personal information securely
- A new exception to reporting data breaches that are unlikely to cause harm
- A new requirement to notify the D.C. Attorney General of a data breach
- New exemptions for HIPAA- and GLBA-compliant organizations
- A new requirement to provide ID theft services to certain data breach victims

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.