The National Institute of Standards (NIST) Privacy Framework provides practical controls and actionable steps that could improve how your organization identifies, manages, and responds to privacy risks.
With new privacy and data protection laws emerging globally, particularly across the U.S., implementing the Framework could help you get a headstart on compliance - and, if your resources allow, develop a mature and effective privacy program.
This article explains how the NIST Privacy Framework works and how to take your first steps toward implementation.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
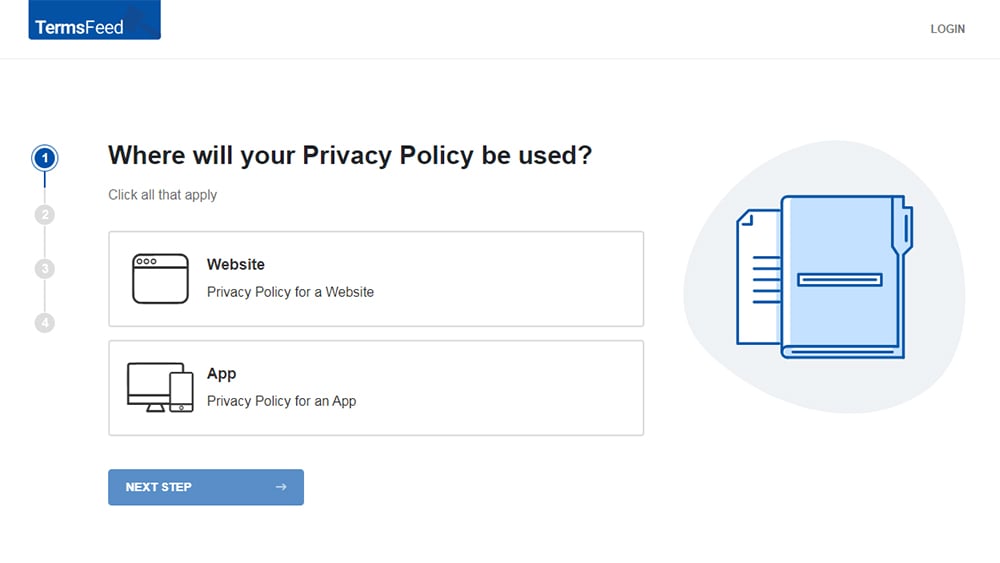
At Step 1, select the Website option or App option or both.
-
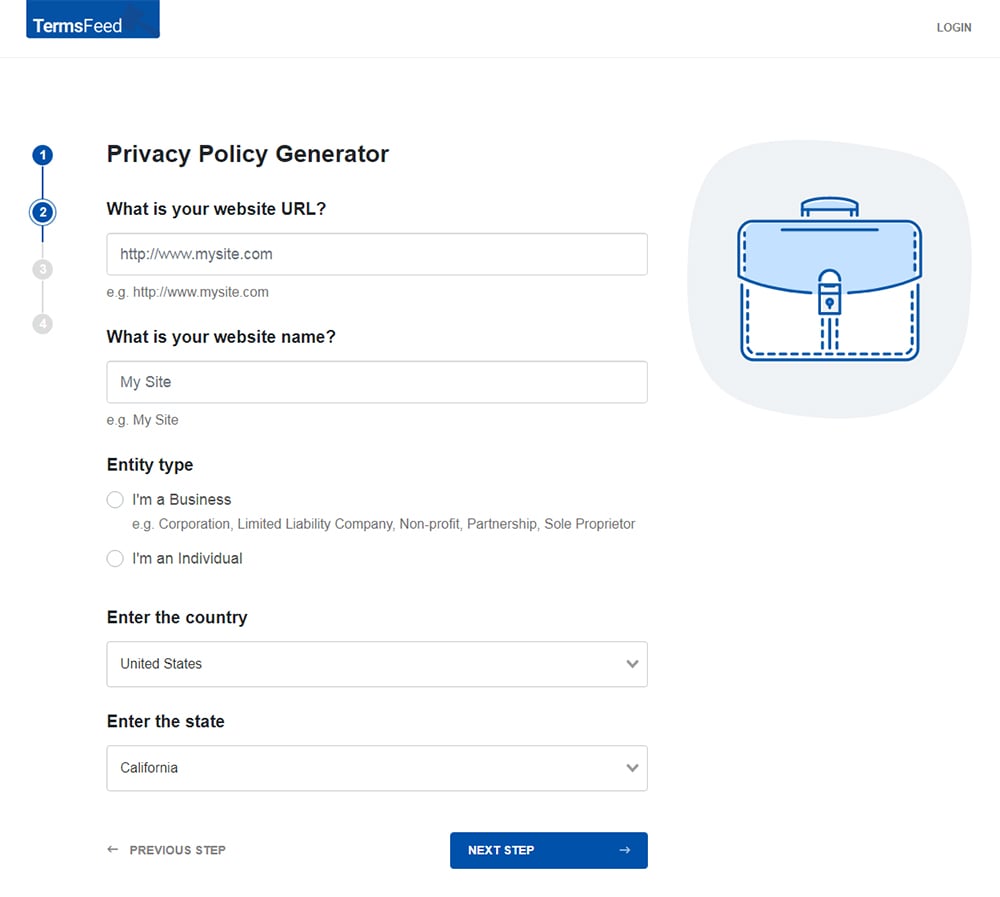
Answer some questions about your website or app.
-
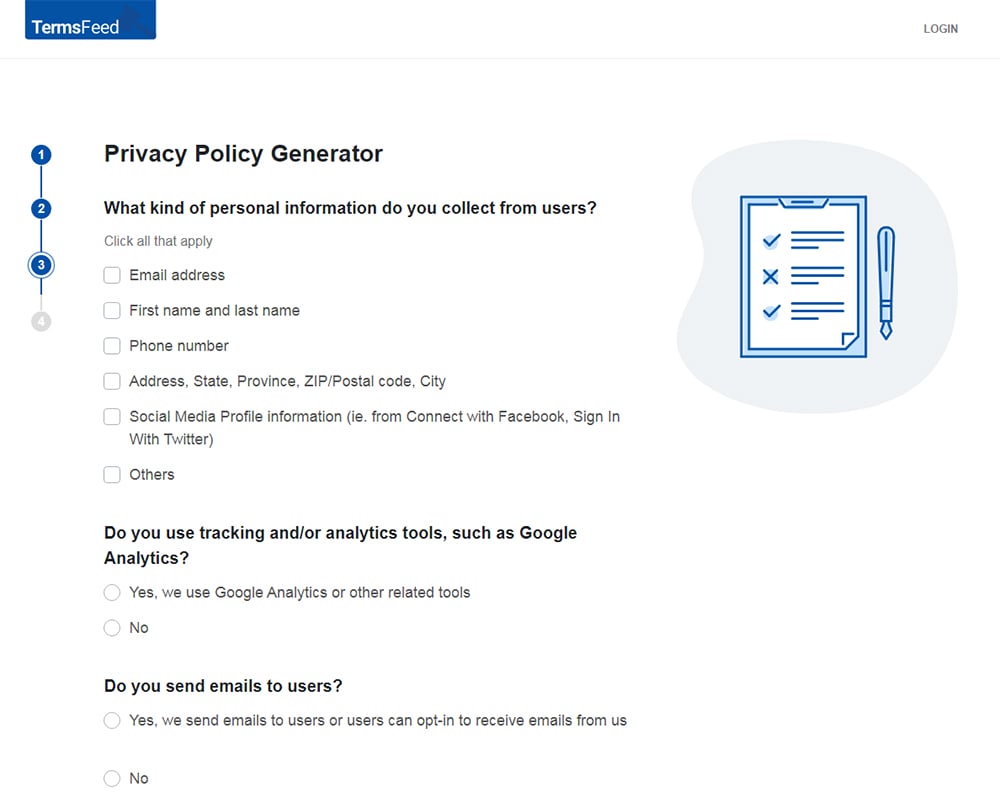
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
You'll be able to instantly access and download your new Privacy Policy.
- 1. What is the NIST Privacy Framework?
- 2. Why Implement the NIST Privacy Framework?
- 2.1. Is the NIST Privacy Framework Optional?
- 3. Outline of the NIST Privacy Framework
- 3.1. Core
- 3.1.1. Functions
- 3.1.2. Categories
- 3.1.3. Subcategories
- 3.2. Profiles
- 3.3. Implementation Tiers
- 4. Using the NIST Privacy Framework
- 4.1. Mapping to Informative References
- 4.2. Strengthening Accountability
- 4.3. Establishing or Improving a Privacy Program
- 5. NIST Privacy Framework Overview
What is the NIST Privacy Framework?
The NIST Privacy Framework ("A Tool for Improving Privacy Through Enterprise Risk Management") is a voluntary system for organizations wishing to improve their privacy risk management practices.
Working through the NIST Privacy Framework is a systematic way of putting privacy controls in place and measuring their effectiveness, all in the context of your organization's sector and resources.
The Framework is built around three parts:
- Core: Privacy protections and outcomes
- Profile: An organization's current privacy posture and desired outcomes
- Tiers: Different levels of implementation of the framework reflecting an organization's resources
Each part of the framework has various sub-parts and associated concepts.
The structure of the Framework can seem a little daunting at first. But as we'll explain, NIST has provided a neat way to systematize your company's processes and work towards improved privacy standards.
Why Implement the NIST Privacy Framework?
There are several reasons why implementing a program such as the NIST Privacy Framework is a good idea for many businesses.
If you're looking for a way to improve your privacy risk management, the Framework is one of several options.
The NIST Privacy Framework is:
- Well-known
- Flexible
- Outcome-focused
The Framework suits businesses of virtually any size, but it's particularly popular among smaller organizations due to its flexibility and progressive structure.
Is the NIST Privacy Framework Optional?
Yes, implementing the NIST Privacy Framework is optional. It's not a legal requirement. But following the Framework, or another respectable privacy risk management standard like ISO 27701, could help with legal compliance.
New privacy and data protection regulations are springing up all over the world. In the United States, a number of states have enacted comprehensive privacy laws. Several more have passed strict sector-specific laws, and a federal privacy law could pass within a few years.
In fact, businesses that have implemented the NIST Privacy Framework are automatically assumed to be compliant with one of these recently-passed privacy laws, the Tennessee Information Protection Act (TIPA) (under certain conditions).
Even if you're not covered by any such legislation, you most likely soon will be - and implementing the NIST Privacy Framework is a great way to start meeting or even exceeding baseline compliance.
But conversely, meeting the Framework's requirements does not necessarily mean you're compliant with most privacy and data protection laws.
Outline of the NIST Privacy Framework

Now let's take a look at how the NIST Privacy Framework is structured and how it approaches privacy risk.
Core
The Core of the NIST Privacy Framework is a way of systematizing the management of privacy risk. The Core is divided into Functions, which again divide into Categories, which further divide into Subcategories.
Here's how NIST explains the Core:
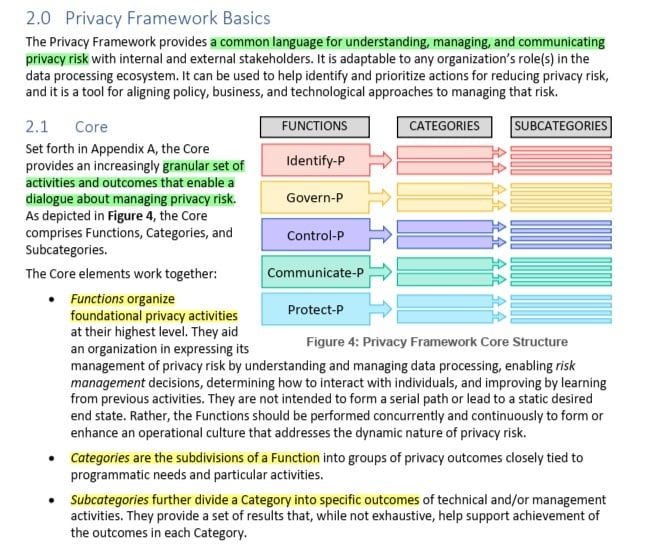
As NIST notes, the Core is "not a checklist." Organizations can take a "risk-based approach," deciding which Subcategories to tackle depending on their resources and operational context.
Functions
Functions are the highest level of the Core: broad, foundational, privacy-related concepts.
Here are the NIST Privacy Framework's eight Functions:
- Identify-P (ID-P): Discovering and assessing privacy risks
- Govern-P (GV-P): Developing high-level strategies and procedures
- Control-P (CT-P): Implementing data processing policies and processes
- Communicate-P (CM-P): Raising awareness and facilitating collaboration
- Protect-P (PR-P): Applying data security and protection controls
- Detect (DE): Searching for threats and anomalies
- Respond (RS): Taking action following an incident or discovery
- Recover (RC): Recuperating and learning from privacy breaches
These Functions are the top level of your privacy program.
Categories
Each of the Core's Functions is divided into Categories, which refine the high-level concepts into groups of activities.
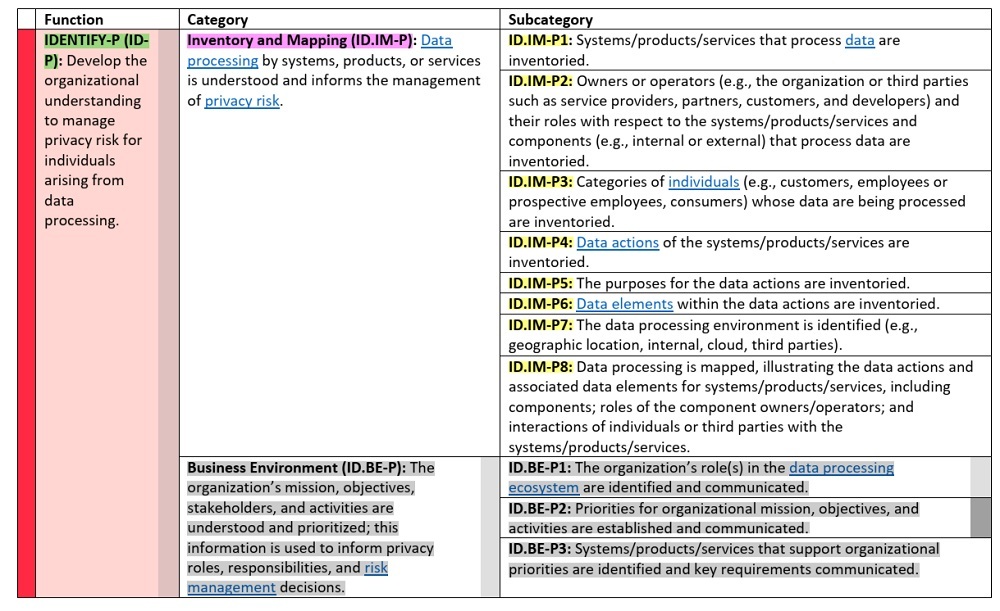
We won't list all of the NIST Privacy Framework's Categories, but here are the Categories associated with the "Identify-P (ID-P)" Function:
- Inventory and Mapping (ID.IM-P): Identifying your data processing systems and data flows
- Business Environment (ID.BE-P): Assessing your business strategy and organizational structure
- Risk Assessment (ID.RA-P): Identifying the risk of harm to individuals and potential follow-on harms
- Data Processing Ecosystem Risk Management (ID.DE-P): Identifying and mitigating risks within the company's processing systems and service provider network
There are nearly 30 categories across the Framework's eight Functions, with some Functions (namely "Protect-P" and "Respond," each of which has six Categories) possessing more Categories than others (namely "Communicate-P," which has only two Categories).
Subcategories
The lowest level of the Core is the Subcategory.
Each Category divides into Subcategories, which identify specific outcomes associated with the type of work required under each category.
Again, we won't list all of the NIST Privacy Framework's Subcategories, but here are the Subcategories falling under the "Business Environment (ID.BE-P)" Category (which falls under the "Identify-P (ID-P)" Function).
- ID.BE-P1: The organization's role(s) in the data processing ecosystem are identified and communicated
- ID.BE-P2: Priorities for organizational mission, objectives, and activities are established and communicated
- ID.BE-P3: Systems/products/services that support organizational priorities are identified and key requirements communicated
Categories can have anything between two and eight Subcategories.
Here's a table from NIST showing a Function with some of its Categories and Subcategories:
Profiles
In practical terms, to build a Profile, you select Functions, Categories, and Subcategories from the Core, as appropriate for your priorities, context, and resources.
Under the NIST Privacy Framework, there are no predetermined Profiles. But there are two broad types of Profiles:
- Current Profile: The privacy outcomes your organization already meets
- Target Profile: The state your organization aims to reach
Here's an example of a Current Profile relating to a hypothetical small business, focusing on Categories and Subcategories of the Identify-P (ID-P) Function.
The Functions, Categories and Subcategories that the business has not achieved (or fully achieved) are highlighted in yellow, and those that the business has achieved are highlighted in green:
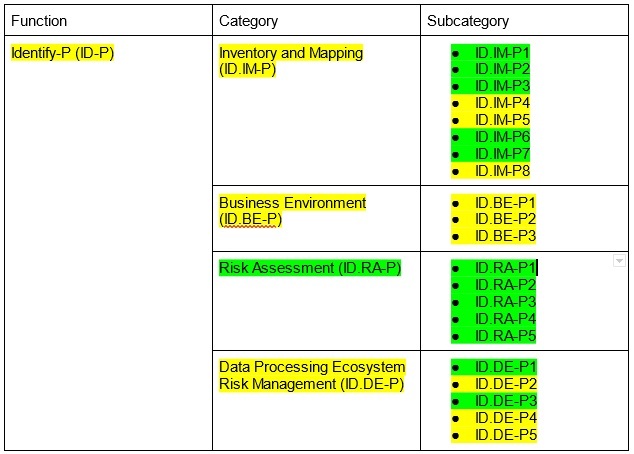
The above hypothetical Current Profile shows that our made-up small business has achieved:
- All of the "Risk Assessment (ID.RA-P)" Category
- None of the "Business Environment (ID.BE-P)" Category
- Some of both the "Inventory and Mapping (ID.IM-P)" and "Data Processing Ecosystem Risk Management (ID.DE-P)" Categories
This Current Profile is the company's starting point (for this specific Function). But remember, the business does not need to cover everything in the NIST Privacy Framework.
To create a Target Profile, our business will need to consider its Implementation Tiers - a concept we'll explain below.
Implementation Tiers
The NIST Privacy Framework establishes four Implementation Tiers, which broadly relate to how an organization views and manages privacy risk.
Here are the Framework's four Implementation Tiers:
- Tier 1: Partial
- Tier 2: Risk Informed
- Tier 3: Repeatable
- Tier 4: Fully Adaptable
The Tiers are progressive: You're aiming to move from a lower Tier to a higher Tier of your choice, e.g. from "Partial" to "Repeatable."
There are four elements that help determine a company's Implementation Tier:
- Privacy Risk Management Progress
- Integrated Privacy Risk Management Program
- Data Processing Ecosystem Relationships
- Workforce
So, for example, here's how our hypothetical small business might operate across these four elements. We'll imagine the business is at Implementation Tier 1 ("Partial").
| Implementation Tier 1 | |
| Privacy Risk Management Process |
|
| Integrated Privacy Risk Management Program |
|
| Data Processing Ecosystem Relationships |
|
| Workforce |
|
Having identified its Current Profile and Implementation Tier, our business better understands the gaps in its privacy risk management practices. The company can then build a Target Profile that helps it move up to Implementation Tier 2 or beyond.
To understand how to put the NIST Privacy Framework into practice, let's look briefly at some other important processes and concepts.
Using the NIST Privacy Framework
Now you understand how the NIST Privacy Framework works, let's look at the practical aspects. Here are three further steps your organization can take to get value out of the Framework.
Mapping to Informative References
The NIST Privacy Framework's "Informative References" sit within the model's Subcategories. These are written as "Crosswalks" that connect the Subcategories to various laws and standards.
Here are some examples of NIST Privacy Framework Crosswalks:
- CCPA Crosswalk by BakerHostetler
- GDPR Crosswalk by Enterprivacy Consulting Group
- VCDPA Crosswalk by BakerHostetler
You can consider exploring one or more of these Crosswalks depending on which privacy laws apply to you.
Strengthening Accountability
Like all privacy-related standards, the NIST Privacy Framework emphasizes the importance of accountability.
Among other things, accountability means identifying who is responsible for managing privacy risk and implementing privacy safeguards, and establishing how people can communicate about privacy risk across the organization.
Establishing or Improving a Privacy Program
The ultimate objective when working with a standard such as the NIST Privacy Framework is to either establish or improve your organization's privacy program.
NIST suggests that there are three stages involved in getting a privacy program off the ground:
- Ready: Using the "Identify-P" and "Govern-P" Functions to develop your Current and Target Profile
- Set: Creating an action plan to help you move from your Current Profile to your Target Profile
- Go: Doing the work. Making the necessary changes to move up achieve your Target Profile and move up one or more Implementation Tiers
NIST Privacy Framework Overview
The NIST Privacy Framework could help you with any of the following:
- Implementing a privacy risk management program for the first time
- Improving your company's existing privacy program
- Working towards compliance with privacy and data protection law
The Framework provides you with activities to undertake, outcomes to achieve, and resources to consult.
Here's a reminder of the structure of the NIST Privacy Framework:
-
The Core: A model of privacy risk management, consisting of:
- Functions: The broadest grouping of privacy risk concepts
- Categories: Types of approaches to managing privacy risk
- Subcategories: Specific privacy risk management actions and outcomes
-
Profiles: A way to describe an organization's privacy risk management posture:
- Current Profile: Where you start out
- Target Profile: Where you want to get
-
Implementation Tiers: A conceptualization of an organization's privacy risk management maturity:
- Tier 1: Partial
- Tier 2: Risk Informed
- Tier 3: Repeatable
- Tier 4: Fully Adaptable

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.