India's IT Act 2000 covers offenses involving computers, computer systems, or computer networks in India. It also makes acts like hacking, data theft, spreading of computer viruses, identity theft, defamation (sending offensive messages), pornography, child pornography, and cyber terrorism criminal offenses, and gives legal validity to electronic contracts and recognition of electronic signatures.
This article will provide a complete overview of the act, including its aims, whom it applies to, and how businesses can comply with it to avoid penalties.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
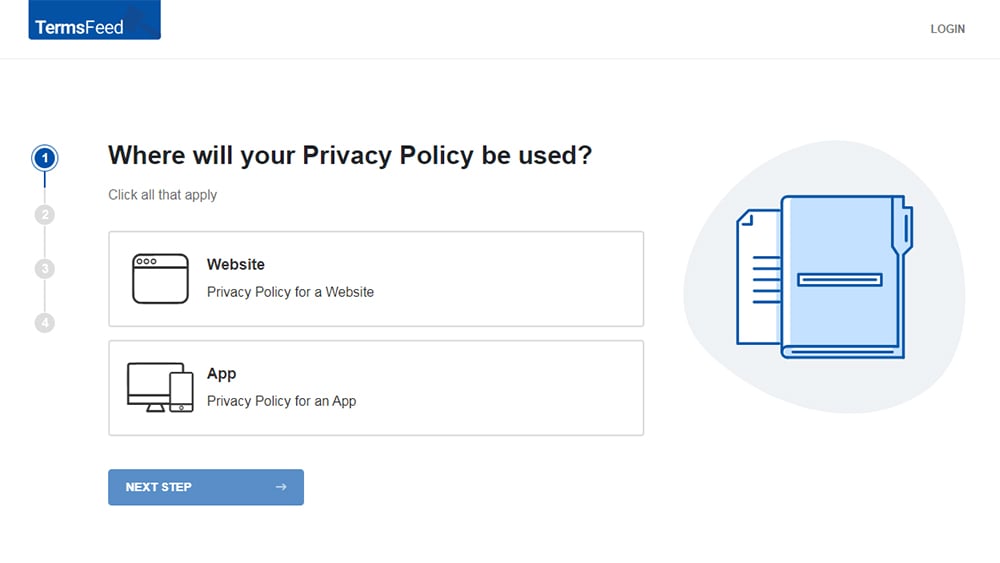
At Step 1, select the Website option or App option or both.
-
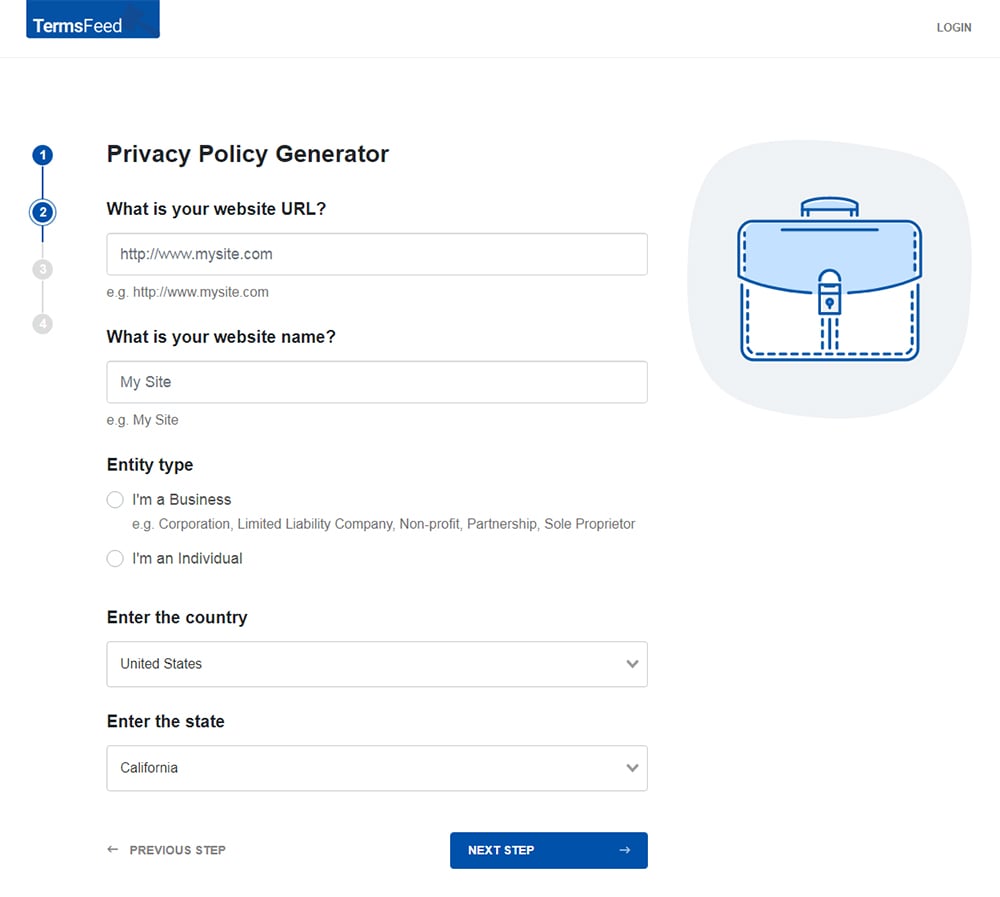
Answer some questions about your website or app.
-
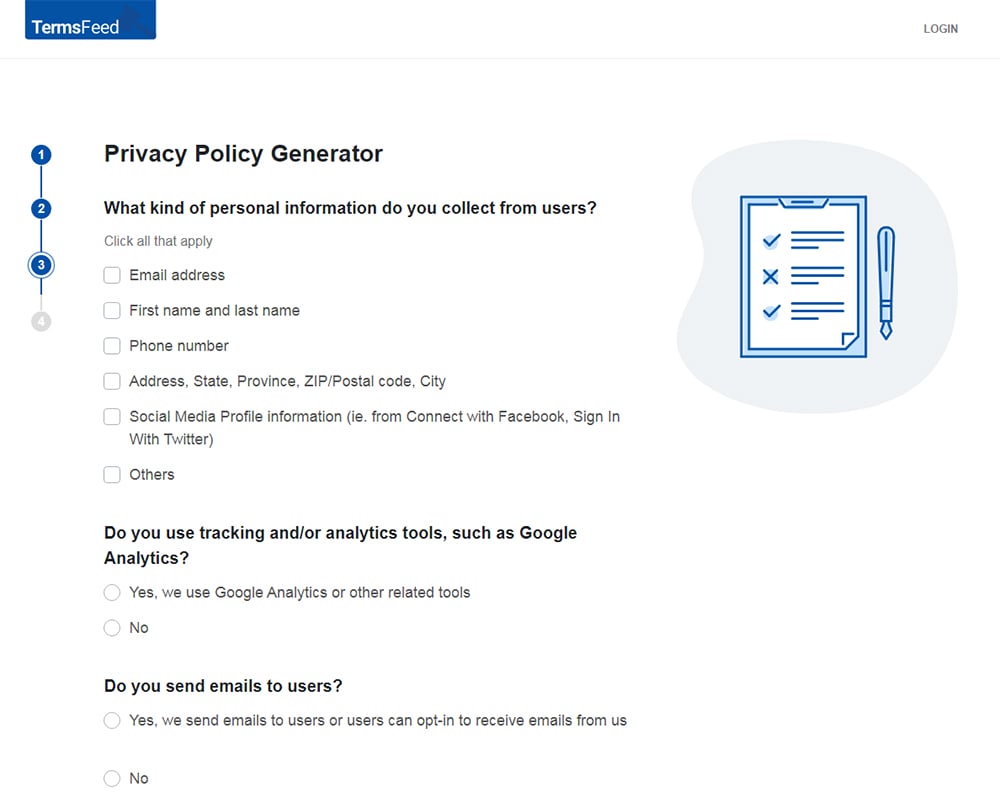
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
You'll be able to instantly access and download your new Privacy Policy.
- 1. The History of the India IT Act of 2000
- 2. To Whom Does the India IT Act of 2000 Apply?
- 3. What are Considered Offenses Under the India IT Act of 2000?
- 3.1. Tampering with Computer Source Documents
- 3.2. Hacking With a Computer System
- 3.3. Receiving Stolen Computers or Communication Devices
- 3.4. Using Another Person's Password
- 3.5. Cheating or Scamming Others Using Computer Resources
- 3.6. Publishing Private Images of Others
- 3.7. Acts of Cyber Terrorism
- 3.8. Publishing Obscene Information Online
- 3.9. Publishing Images Containing Sexual Acts
- 3.10. Failure to Maintain Records
- 3.11. Failure or Refusal to Comply With Government Orders
- 3.12. Failure or Refusal to Decrypt Data
- 3.13. Securing Access to a Protected System
- 3.14. Misrepresentation
- 3.15. Corporate Bodies are Liable for Sensitive Information
- 4. How to Comply with the India IT Act of 2000
- 4.1. Know Where Your Servers are Located
- 4.2. Follow a Privacy By Design Framework
- 4.3. Always Acquire Written Consent
- 4.4. Pay Attention to User-Generated Content
- 5. Conclusion
The History of the India IT Act of 2000
In order to encourage this growth and protect India's intellectual property (IP), the Indian government enacted the India IT Act of 2000 (ITA-2000).
The Information Technology Act of 2000 came into force on October 17, 2000. This act is imposed upon the whole of India. Its provisions apply to any offense committed inside or outside India's geographic boundaries and irrespective of nationality.
It's founded upon the 1996 United Nations Model Law on Electronic Commerce (UNCITRAL Model), which the United Nations General Assembly suggested through a resolution on January 30, 1997.
Today, the India IT Act of 2000 is the most important law in India dealing with ecommerce and cybercrime. It is also considered one of the strictest privacy laws in the world, and to avoid potential penalties, those who operate from India need to understand what's in it.
For instance, the IT Act has 13 chapters and 90 sections. The last four sections deal with revisions to the Indian Penal Code. The Indian government revised the law several times, inserted four new offenses, and enhanced the punishment for the existing eight computer-related crimes.
The legal principles pertaining to information technology law in India are mostly assimilated from previous standards enacted earlier in several other countries.
These principles are augmented by a staggering number of rules, which include regulations on everything mentioned previously, as well as the following:
- Cyber cafes
- Electronic service delivery
- Data security
- Blocking websites
Any person who is a victim of data theft, hacking, or spreading of viruses can apply for compensation from the Adjudicator appointed under Section 46 of the Act. The Adjudicator will review the case and decide if compensation is warranted.
Suppose the Adjudicator decides that compensation is warranted. In that case, the person will be able to receive compensation from the company or individual responsible for the data theft, hacking, or spreading of computer viruses.
The Appeal from the Adjudicator lies with the Cyber Appellate Tribunal. The Cyber Appellate Tribunal will review the case and decide if the Adjudicator was correct in their decision.
To Whom Does the India IT Act of 2000 Apply?

The IT Act 2000 is applicable to companies that do business in India, including entities registered in the country, ones that outsource there, and ones that maintain servers within the country's borders.
The act covers all activities that involve electronic documents and online exchanges.
If your only connection to India is having customers there, you are not bound by the IT Act. The only way that can occur is to run a service or sell a product and maintain servers there.
Take Amazon, Walmart, and the U.S.-based footwear company Skechers, for example. Each is an American company that has offices in India.
Because they have a physical presence and operate electronically within the country's borders, they are bound by the provisions of the law.
On the other hand, Pinterest has many regional offices around the globe, but none in India. Still, around 23 percent of India's social media users engage on Pinterest.
However, the bottom line is that because Pinterest does not operate physically within India's borders, the country's law doesn't apply to the company.
What are Considered Offenses Under the India IT Act of 2000?

The IT Act contains a list of offenses and corresponding punishments. Some of the more severe violations include tampering with computer source documents, hacking, receiving stolen computers, using another person's password and others.
Let's look deeper at these and others.
Tampering with Computer Source Documents
Computer source code is the set of instructions that tell a computer what to do. It is the foundation of all computer programs, systems, and networks. If a person knowingly or intentionally destroys, conceals, or alters computer source code, they could be sentenced to imprisonment of up to three years and/or a fine of up to RS 200,000 (Indian rupees).
This offense is taken seriously because computer source code is vital for the functioning of our increasingly digital world. Altering or destroying it can cause serious harm to computer systems and networks, and ultimately people.
Hacking With a Computer System
If a person hacks with the intent to cause wrongful loss or damage to the public or any person, they can be faced with a penalty of three years in prison as well as a fine of up to 500,000 rupees.
As advanced technology progressively becomes a part of our day to day lives, it's essential to be aware of the risks that sometimes come with it.
One such risk is hacking, which is defined in the IT Act of 2000 as the unauthorized access or destruction of information residing in a computer resource.
Receiving Stolen Computers or Communication Devices
The penalties for taking possession of a stolen computer resource is up to three years in jail. You could also be fined up to 100,000 rupees.
Computer resources are broadly defined to include all types of computer data, programs, files, and computer hardware and devices.
Using Another Person's Password

In India today, it's a severe offense to fraudulently use another person's password, digital signature, or other unique identification.
If caught, you could face imprisonment for up to three years and/or a fine of up to RS 100,000. It's, therefore, best to make sure you only use your own login credentials and never share them with anyone else.
An excellent way to do that is to invest in a password manager such as one of the following:
- Bitwarden
- Dashlane
- 1Password
- LastPass
Password managers provide a secure, centralized repository for all your passwords, making it easy for you to keep track of them all.
It also offers several other benefits including generating strong passwords, logging in to websites automatically, and filling in web forms with your personal information.
Cheating or Scamming Others Using Computer Resources
Cheating people using computer resources is a serious offense, and the penalty for doing so is imprisonment of up to three years or/and with a fine of up to RS 100,000.
Computer resources can be used to cheat people. For example, a person might create a fake website that looks like a legitimate business. Then, they could use this website to collect personal information or money from unsuspecting victims.
Publishing Private Images of Others
Under the IT Act of 2000, if a person captures, transmits, or publishes images of another person's private parts without that individual's consent or knowledge, the perpetrator may be subject to a prison sentence of up to three years. A fine of up to 200,000 Rupees may also be levied.
In India today, there are many cases of people being coerced into having their private parts photographed or filmed without their knowledge or consent. This is a serious violation of their rights and can have a lasting impact on their lives.
The penalty is harsher if the victim is a minor.
Acts of Cyber Terrorism
Cyber terrorism is a severe offense in India, punishable by up to life in prison. If a person denies access to authorized personnel to a computer resource or accesses a protected system to threaten India's unity, integrity, sovereignty, or security, he has committed cyber terrorism.
Publishing Obscene Information Online
Publishing or transmitting any sort of lewd or licentious material in electronic form is punishable by imprisonment of up to five years. A significant fine of up to RS 1,000,000 could also be handed down.
The government brought about this change in order to protect children and other vulnerable persons from being exposed to harmful or offensive content. It is crucial to be conscious of this law in order to avoid inadvertently breaking it.
If you are unsure about whether something you are planning to publish falls into this category, it is wise to exercise prudence and consult with your legal department beforehand.
Publishing Images Containing Sexual Acts
While sexually explicit material is not illegal in India per se, there are restrictions on its distribution and sale. It is punishable to sell, distribute, exhibit, circulate, import, or export any obscene picture, painting, writing, book, or pamphlet through electronic means which is lustful or lewd or depraved, or corrupts another person.
Additionally, if a person transmits images containing a sexual explicit act or conduct, for instance through email, they may be subject to imprisonment for up to seven years and/or a fine of up to RS 1,000,000.
Thus, while sexually explicit material is not illegal in India, its dissemination has definite restrictions.
Failure to Maintain Records

An intermediary is defined as a person who provides an information system or platform for electronic commerce. This can include ISPs, social media platforms, and ecommerce websites. Under the law, intermediaries are required to maintain certain records for a stipulated period.
These records must be kept at the disposal of law enforcement agencies. Failure to comply with this requirement is an offense, punishable by imprisonment of up to three years, or/and a fine.
Failure or Refusal to Comply With Government Orders
Businesses and their employees are required to take specified measures or cease carrying on specified activities if authorities believe that such actions are necessary to ensure compliance with the IT Act of 2000.
Any person who fails to obey such an order is guilty of an offense, punishable by up to three years in prison. That individual may also have to pay a fine of up to RS 200,000.
Failure or Refusal to Decrypt Data
Government authorities in India have the authority to intercept any information transmitted through computer resources under the following conditions:
- It is essential or desirable to do so in the interest of the sovereignty or integrity of India
- It is essential or desirable to do so in the interest of the security of the State
- It is essential for relations with foreign States
- It is essential or desirable to do so in the interest of public order, or
- It is essential or desirable to do so in the interest of preventing incitement to the commission of any cognizable offense
The subscriber or any person in charge of the computer resource must extend all facilities and assistance for carrying out such interception when called upon by any agency that has been directed.
Failure or refusal to decrypt data for the authorities involved carries a penalty of a potential fine and a sentence of up to seven years in prison.
Securing Access to a Protected System
In India, the appropriate government may, by notification in the Official Gazette, declare that any computer, computer system, or computer network is a "protected system."
A protected system means a computer, computer system, or computer network which is:
- Empowered by law or any rule or regulation made thereunder to send or receive messages or communicate with other computers
- Specially protected by law or any rule or regulation made thereunder from unauthorized access or misuse, and
- Communicated over a communication device including telephone lines, optical fiber cables, satellites, microwave transmission, and others
If a person gains access or attempts to secure access to a protected system, then that individual is committing an offense and could face imprisonment of up to ten years. A fine may also be levied.
Misrepresentation
If anyone makes any misrepresentation to or conceals any material fact from the relevant authorities for obtaining any license or Digital Signature Certificate, they may face a penalty of up to three years in jail. They may also be fined up to RS 100,000.
Corporate Bodies are Liable for Sensitive Information
Under the law, a corporate body that deals with sensitive information is responsible for ensuring that acceptable security practices are in place to protect that information.
If the corporate body fails to do so and the sensitive information is lost, the corporate body will be held liable.
This is why it is essential for corporate bodies to take security seriously and to have measures in place to prevent sensitive information from being lost.
Some of these measures include encrypting sensitive data, storing it in a secure location, and restricting access to it.
How to Comply with the India IT Act of 2000

Privacy requirements are essential for any business, but especially for companies that collect or store sensitive information about consumers. The IT Act and the following privacy requirements are designed to protect consumers' information from being accessed or used without their consent.
Complying with these provisions can be time-consuming and expensive. Still, it is essential for protecting your customers' privacy and for keeping your business (and yourself) out of trouble with India's legal system.
Know Where Your Servers are Located
The IT Act of 2000 is super strict as it pertains to intermediaries. These intermediaries, which can include anything from companies that own servers to consultants who handle outsourcing, are held responsible for the content that is on their servers.
This means that if your company is located in India or if it outsources to India, you must ensure that all of your content complies with Indian law.
Failure to do so could result in serious consequences. Of course, knowing where your servers are located is not always easy. Companies often outsource their IT needs to other firms, which can lead to multiple layers of outsourcing.
If you are not sure where your servers are located, ask your IT provider.
Follow a Privacy By Design Framework
Privacy by Design (PBD) starts with the assumption that any system handling personal information should be designed with privacy in mind and that you should build privacy into every stage of development.
Your privacy protection practices go well beyond having a good Privacy Policy. That's just one tool to protect your company from liability and communicate expectations with users. Still, it's not effective if you don't have the business policies to back it up.
That is where PBD comes into the picture. Together with advocating for sound agreements and good communication, it also recommends systems to ensure that the data you collect from users remains safe.
By taking this comprehensive approach, you can help to ensure that your company's privacy protection practices are genuinely effective.
Always Acquire Written Consent
The 2011 privacy protection additions passed by India's government require written permission from users before a company can use personal information.
Many companies have considered these burdensome, as they must now take extra steps to ensure they have the proper permissions in place.
Pay Attention to User-Generated Content
If you offer an app or online service that involves exchanging material, it's vital to develop screening procedures so you can control user-generated content before it posts.
Just as avoiding security breaches can help you stay in compliance with ecommerce protection and cybersecurity laws, taking the same approach to potentially illegal content will help you reduce the risk of legal liability.
Implementing extensive moderation procedures will enable you to control the content that is posted on your site or app. By following these preventive measures, you can help ensure that your online service or app is a welcoming and safe environment for everyone.
Conclusion
The India IT Act of 2000 is a law that seeks to protect people's privacy and personal information online. The law applies to all businesses and individuals who collect, process, or store personal data and maintain a physical business presence within India's borders.
It also applies to third-party intermediaries who own and maintain servers within India.
To comply with ITA-2000, businesses and individuals must take steps to protect people's personal information from being mishandled or misused and be cognizant of various other regulations surrounding electronic devices and networks.
Companies would be well advised to begin with a Privacy by Design approach when it comes to complying with India's data privacy regulations.
This means incorporating privacy into all aspects of their business, from the systems they use to their agreements with customers.
It also requires writing clear and concise Privacy Policies that everyone can understand.
Companies should also have stringent conduct standards in place and monitor their systems closely to ensure everyone complies with them.
Finally, a best practice is to have a dedicated attorney or legal department to help navigate your company through the murky regulations of India's ecommerce and cybersecurity law.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.