The COVID-19 pandemic has seen workplaces, universities, and consumers move online. Now more than ever, consumers are placing their trust in online businesses. And businesses are finding new challenges in conducting more of their operations online.
Perhaps unsurprisingly, cybercriminals are finding ways to exploit the situation, and there has been a significant increase in threats to personal and sensitive information.
It's now more important than ever to ensure you're properly protecting customers' privacy and your company's security.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
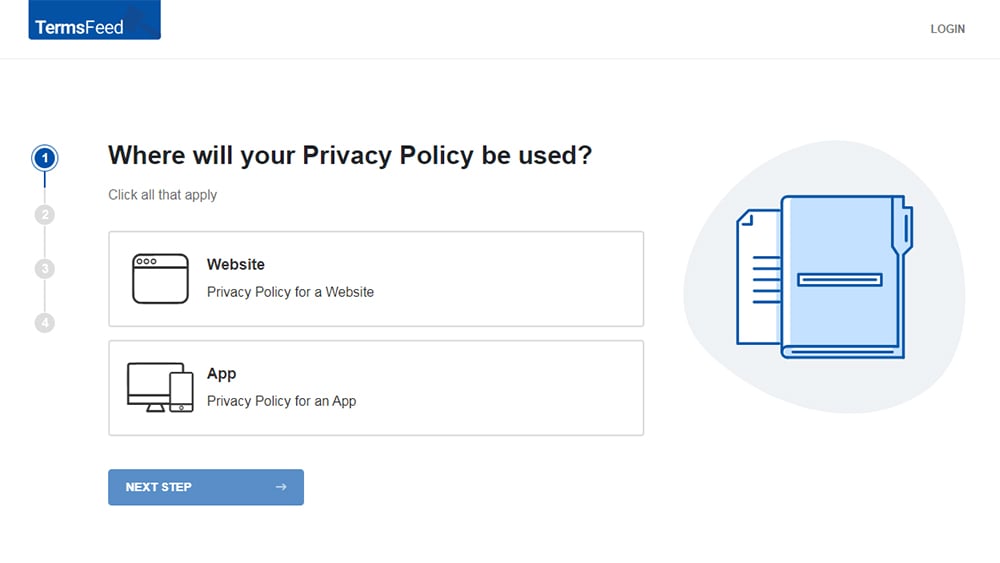
At Step 1, select the Website option or App option or both.
-
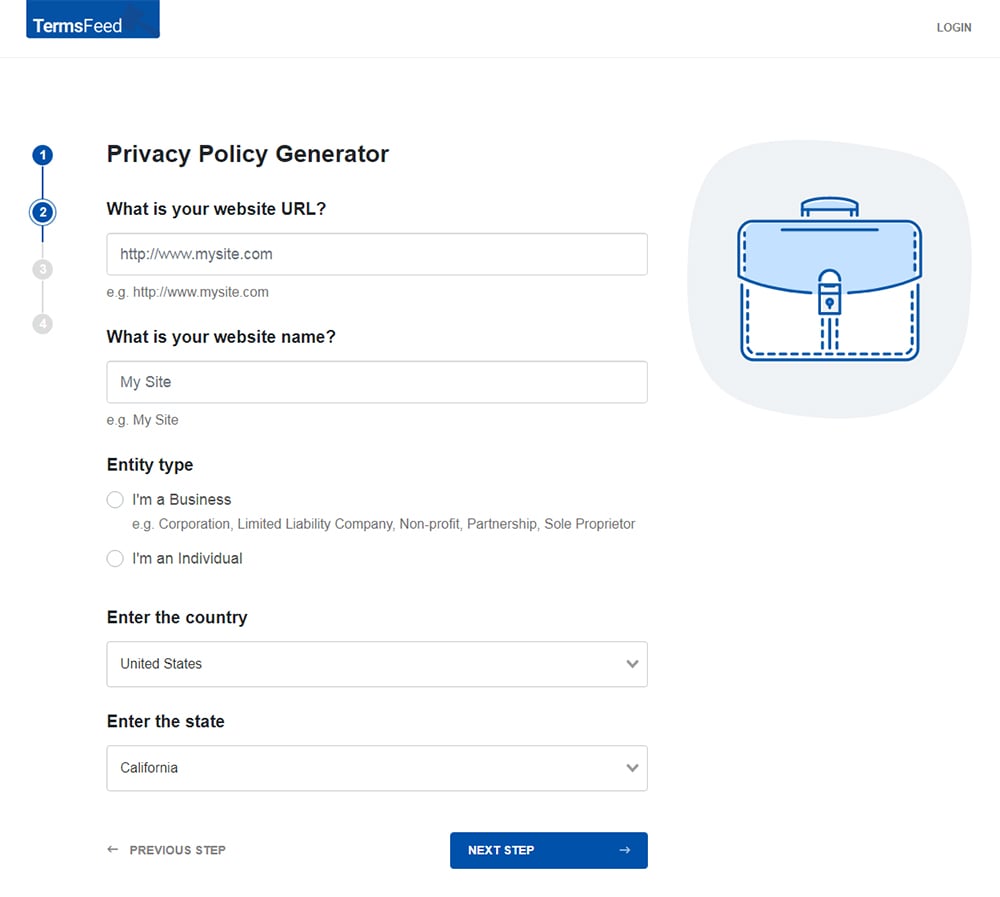
Answer some questions about your website or app.
-
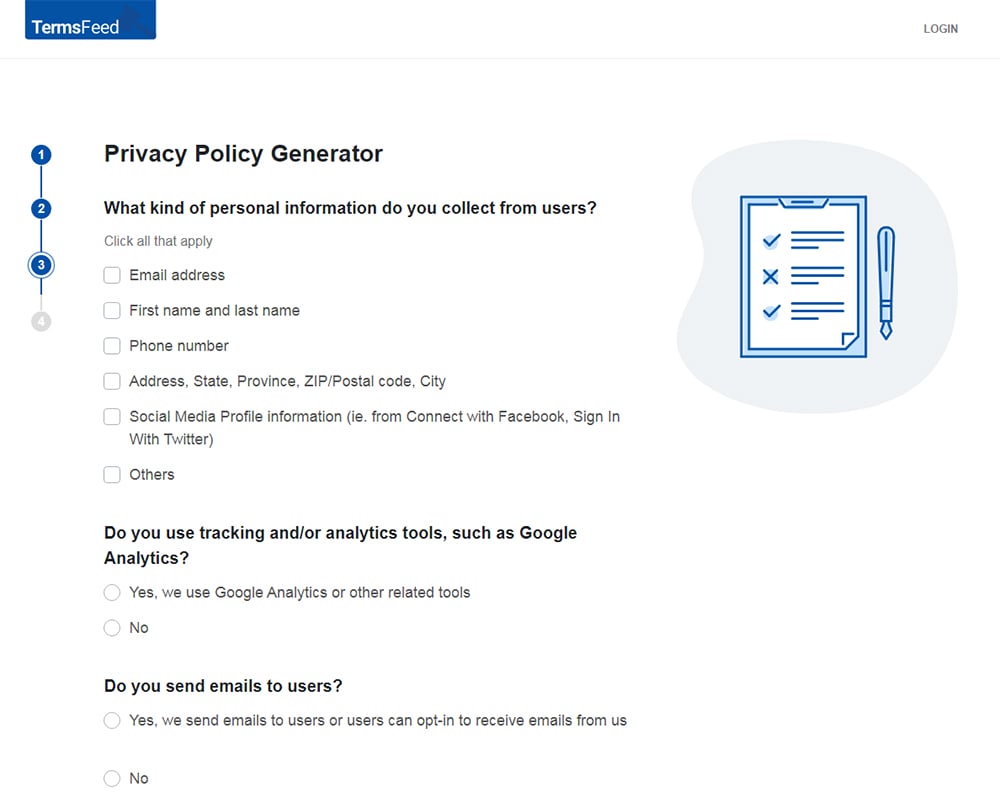
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
You'll be able to instantly access and download your new Privacy Policy.
- 1. COVID-19 Privacy and Security Threats
- 1.1. Phishing
- 1.2. Malware
- 1.3. Consumer Confidence
- 2. Understanding Your Legal Obligations
- 3. Administrative Privacy and Security Safeguards
- 3.1. Designating an Accountable Employee
- 3.2. Assess Risks to Privacy and Security
- 3.2.1. Identifying Risks
- 3.2.2. Assessing the Likelihood and Severity of Risks
- 3.3. Creating Security and Privacy Policies
- 3.3.1. Privacy Policy
- 3.3.2. Data Protection Policy
- 3.3.3. IT Security Policy
- 4. Physical and Technical Safeguards
- 4.1. Technical Safeguards
- 4.1.1. Security Software
- 4.1.2. Password Management
- 4.2. Physical Safeguards
- 4.2.1. Preventing Intrusion
- 4.2.2. Disposing of Files and Equipment
- 5. Summary
COVID-19 Privacy and Security Threats
Let's look at some of the online threats we've seen emerging during the COVID-19 pandemic.
Phishing
Phishing is a common type of online scam that involves tricking people into giving up personal or sensitive information, typically account credentials or payment card details.
IT security firm KnowBe4 reports that there has been a staggering 600% rise in phishing scams, attributable in part to a widespread fake message purporting to be from the Center for Disease control about COVID-19.
The U.S. Treasury is encouraging people to report COVID-19-related scams.
Malware
Computer viruses have long represented a threat to business. But viruses are just one type of malware (malicious software), including ransomware, spyware, and bots.
Antivirus company Bitdefender has published data suggesting that malware developers are busier than ever, using COVID-19-themed messages to trick people into installing malware.
Staff working from home are particularly vulnerable to malware, which can go undetected if on any device without adequate anti-malware software installed.
Consumer Confidence
With governments developing potentially-invasive COVID-19 "contact tracing apps," with or without Apple and Google's involvement, public concerns about online privacy are at an all-time high.
Now is the opportunity for you to implement the very best security practices, and to create policies that will demonstrate your commitment to your customers' privacy.
Let's look at some of the practical steps you can take to do this.
Understanding Your Legal Obligations

The first step to improving your company's privacy and security practices is to understand what laws apply to you.
Depending on where your company is based, and where your customers are based, there may be several privacy and security laws you need to comply with.
Here are some examples:
- United States (US): The California Online Privacy Act (CalOPPA), California Consumer Privacy Act (CCPA), New York Shield Act, and Nevada's SB 220 apply to any companies operating within those respective states.
- European Union (EU): The General Data Protection Regulation (GDPR) and the ePrivacy Directive
- United Kingdom (UK): The GDPR, Privacy in Electronic Communications Regulations (PECRs) and Data Protection Act 2018
- Canada: Personal Information and Privacy of Electronic Documents Act (PIPEDA)
- Australia: Privacy Act
- South Africa: Processing of Personal Information Act (POPI Act)
You must understand and be accountable under whatever laws apply to your company. If you suffer a data breach or security incident, you will need to demonstrate what steps you have taken to achieve legal compliance.
Administrative Privacy and Security Safeguards

Safeguarding personal and sensitive within your company requires a solid administrative foundation.
Designating an Accountable Employee
You should designate an employee (or, if appropriate, hire a contractor) to oversee and be accountable for, your company's data privacy and security practices.
Designating a person to act as your company's Privacy Officer, IT Security Officer or Data Protection Officer will help ensure your company approaches privacy and security in a more methodical and organized way.
There are several privacy laws that require companies to designate an accountable employee.
- NY Shield Act: Covered entities must designate a person to oversee the Data Security Program.
- HIPAA: Section 164.530(a)(1) of the law (available here) requires covered healthcare organizations to designate personnel to oversee privacy and security.
-
GDPR: Appointing a Data Protection Officer is mandatory for any GDPR-compliant organization which:
- Has over 250 employees, or
- Processes special category data (sensitive personal information) or criminal conviction data on a non-occasional basis, or
- Engages in large-scale behavioral monitoring
- PIPEDA: Canadian private sector organizations must appoint a Privacy Officer who is accountable for complying with the act.
These laws have different requirements for the accountable employee's roles and responsibilities. Typically, these will include:
- Conducting staff training around matters of privacy and security
- Liaising with customers and members of the public on matters of privacy and security
- Liaising with the authorities if there has been a complaint or a data breach
Assess Risks to Privacy and Security

Protecting personal and sensitive information requires a comprehensive understanding of where threats are likely to arise. This means continually assessing risk.
Risk assessment can be a two-stage process:
- Identify risks
- Determine their likelihood and potential severity
Some laws have a specific set of requirements for carrying out a risk assessment, such as the GDPR Data Protection Impact Assessment.
Identifying Risks
Risks can be internal or external.
You may be open to risks through the negligence of your employees or contractors.
You may also be at risk from malicious actors, either from inside or outside of your company.
It's not possible to list all the possible risks to your company's privacy and security. For example, any of the following scenarios could be a risk to privacy and security:
- Leaving your phone on the bus
- Installing a computer on your network without malware protection
- Failing to fix broken keycard scanner
- Hiring a careless subcontractor
Create a list of potential security risks in your company. Here are some ways to identify risks:
- List all the locations in which you store personal or sensitive information
- Consider who has access to the information
- Determine whether the information is accessible off-premises (e.g. through employees' personal devices)
- List all service providers who have access to the information
Assessing the Likelihood and Severity of Risks
For each risk you have identified, consider:
- Likelihood: Is it unlikely, quite likely, or very likely that the risk results in a privacy or security breach?
- Severity: Would the harm caused by the breach be minimal, significant, or severe?
Using this assessment you can rank risks according to their overall risk level.
Creating Security and Privacy Policies

You must have a robust set of internal and external policies. This helps to ensure that everyone in your company is on the same page. It allows you to act quickly in the event of a security incident or data breach. It also allows you to demonstrate accountability to the authorities.
Privacy Policy
A Privacy Policy is a public-facing document that explains all aspects of your company's privacy practices.
Almost every business is required to have a Privacy Policy, regardless of size or industry. Even if your business is not customer-facing it is likely to need to have a Privacy Policy.
The contents of your Privacy Policy will vary depending on the region in which your company or customer base is located, your industry, your company's size, and the ways in which you process personal information.
Here's a breakdown of some of the privacy laws you might need to obey when creating your Privacy Policy.
| Country | Privacy Laws |
| United States | All commercial websites or apps accessible in California must comply with aCalOPPA. This law requires website operators to maintain a Privacy Policy detailing:
|
| European Union | The GDPR requires all data controllers to maintain a Privacy Policy detailing, at a minimum:
|
| United Kingdom | The UK still follows the EU's GDPR. Therefore, the UK's Privacy Policy requirements are the same as in the EU. |
| Canada | PIPEDA requires private sector organizations to maintain a Privacy Policy detailing:
|
| Australia | The Privacy Act 1988 requires every covered business to maintain a Privacy Policy detailing:
|
You should ensure your Privacy Policy is easily accessible via your company's website and/or app.
Data Protection Policy
A Data Protection Policy in an internal document that sets out the standards for handling personal and sensitive information.
Typical sections in a Data Protection Policy may include:
- A summary of the values you expect staff to uphold when handling personal or sensitive data
- The roles and responsibilities of staff
- A procedure for allowing people to access their personal information
- Rules around how to store personal information
- Instructions on how to respond to a data breach
- Rules around disclosing personal information
- Minimum standards for staff training
IT Security Policy
An IT Security Policy is helpful if your staff access personal or sensitive information across many different devices. It helps ensure that all employees are maintaining a reasonable standard of information security at all times.
An IT Security Policy might contain some of the following sections:
- A summary of the laws and regulations dictating how employees use IT equipment
- Roles and responsibilities members of staff
- Rules around backing up company data
- Minimum standards for your IT network
- Rules for use of company email accounts
- Rules for using company devices
- Password management policy
If you are meeting certain standards, such as ISO 20071, your IT Security Policy will need to be created around these.
Physical and Technical Safeguards

Once you have identified the risks to personal or sensitive information in your company, you should put safeguards in place to protect it.
As a matter of good practice, always apply the following principles:
- Do not collect personal information unless you need it in relation to a specific purpose
- Delete information you no longer need
- Always apply reasonable safeguards that reflect the sensitivity of information
Technical Safeguards
Technical safeguards are the methods by which you can strengthen your IT and network infrastructure to safeguard any personal or sensitive data you hold in electronic form.
Security Software
Installing anti-malware software on all staff terminals is essential. Make sure:
- It comes from a reputable online security firm
- It detects all types of malware, including ransomware
- It allows real-time protection (not just scheduled scans)
- It can be centrally administered across multiple endpoint terminals
Do not allow staff to access company materials unless they are using a device protected by anti-malware software.
In the current circumstances, you may also wish to consider setting up a company Virtual Private Network (VPN) for home-working employees.
Password Management
Poor password habits lead to data breaches in a significant majority of cases.
Using password manager software is a good way to ensure that staff employ strong passwords, change them regularly, and store them securely.
Popular password manager brands such as LastPass, Dashlane, and 1Password have enterprise packages that will help you manage your staff's passwords remotely without ever compromising their privacy.
Physical Safeguards
Physical safeguards protect your equipment and premises, both from attacks and hazards.
Preventing Intrusion
As well as cyberattacks, your company needs to be able to detect, prevent, and respond to intrusions on its physical premises.
Consider whether any of the following measures would be appropriate for your company:
- Security passes
- ID badges
- CCTV (ensure you properly consider the privacy implications)
- Security personnel
You should conduct regular audits, checking that keys, security passes, and access permissions are up to date. Ex employees and contractors must return any passes or ID badges.
Disposing of Files and Equipment
When you no longer need personal or sensitive information you must delete or destroy it. Data retention periods can be detailed in your Data Protection Policy.
Physical safeguards cover information stored on paper and on hardware.
Paper files should be shredded and disposed of via a reputable contractor.
There are several options for disposing of information stored on hardware.
- Using software to erase disc contents
- Using magnetic fields to permanently erase information (degaussing)
- Disassembling equipment to render information inaccessible
Summary
The COVID-19 pandemic represents an opportunity for your business to improve its privacy and security practices.
- Conduct a thorough risk assessment, identifying all internal and external risks and ranking them by likelihood and severity.
- Create a Privacy Policy to ensure your customers know you're taking their privacy seriously.
- Create internal documents, such as a Data Protection Policy and IT Security Policy will minimize the likelihood that you suffer a data breach.
- Implement technical and physical safeguards to protect the personal and sensitive information in your company's possession.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.