The Computer Misuse Act 1990 is the UK's legal defense against hacking, allowing the state to prosecute those who use or access computers for malicious purposes.
Understanding this law is a key way for businesses with UK operations to keep cybercriminals out of their systems.
This article will break down what this law does, what are offenses under its scope and what the penalties are for violating it.
What customers say about TermsFeed:
This really is the most incredible service that most website owners should consider using.
Easy to generate custom policies in minutes & having the peace of mind & protection these policies can offer is priceless. Will definitely recommend it to others. Thank you.
- Bluesky's review for TermsFeed. Read all our testimonials here.
With TermsFeed, you can generate:
- 1. About the Computer Misuse Act 1990
- 1.1. What Counts as a "Computer?"
- 1.2. Where Does the Computer Misuse Act 1990 Apply?
- 1.3. Is the Computer Misuse Act 1990 Effective?
- 2. Important Note
- 3. Offenses Under the Computer Misuse Act 1990
- 3.1. Offense 1: Unauthorized Access to Computer Material
- 3.1.1. Important Note
- 3.2. Offense 2: Committing or Facilitating Further Offenses
- 3.3. Offense 3: Intent to Impair the Operation of a Computer
- 3.4. Offense 4: Unauthorized Acts Causing Serious Damage
- 3.5. Offense 5: Making, Supplying or Obtaining Articles for Use in Other Offenses
- 4. Penalties for Violating the Computer Misuse Act 1990
- 4.1. Penalties on Summary Conviction
- 4.2. Penalties on Indictment
- 5. Summary
About the Computer Misuse Act 1990
The Computer Misuse Act criminalizes several acts, including accessing data without authorization (i.e. hacking) and installing malware (e.g. computer viruses, spyware, or ransomware) on a person's computer.
What Counts as a "Computer?"
The term "computer" is intentionally left undefined in the Act. This is in order to give the courts some flexibility, in light of rapid changes in technology.
Consider the definition provided in the case of DPP v McKeown, DPP v Jones: "a device for storing, processing and retrieving information."
Or the following definitions, from the Council of Europe's Convention on Cybercrime (available here):
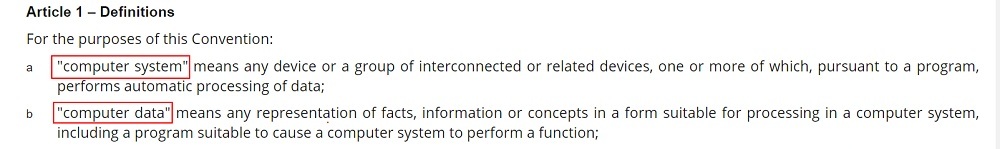
It's reasonable to interpret "computer" as including desktop computers, laptops, mobile devices, and servers.
Where Does the Computer Misuse Act 1990 Apply?

The Act can be used to prosecute crimes with a "significant link" to the UK. This can mean any of the following scenarios:
- The person was located in the UK when they committed the crime
- The target computer was located in the UK
- The person used a server located in the UK to help them commit the crime
- The crime caused (or risked causing) significant damage in the UK
These rules also apply to conspiracy to commit an offense under the Act (e.g. planning to hack a computer that is located in the UK while located abroad).
Is the Computer Misuse Act 1990 Effective?
The Computer Misuse Act is over 30 years old. Three decades is a long time in tech. The Act has been amended several times over the years to add offenses covering cyber-terrorism and malware development, but still may not be up to par.
According to tech website The Register, 422 cases were prosecuted under the Act between 2008 and 2018. Of these, 76 percent of cases resulted in a "guilty" verdict, which is a relatively high conviction rate. This suggests that the law is an effective tool against cybercrime.
However, only 16 percent of those convicted were immediately sentenced to prison, with a further 29 percent given a "suspended sentence" (meaning that the defendant can avoid prison if they meet certain conditions for a given time period).
Critics also say that the Act fails to recognize the value of "ethical" or "white hat" hacking, and could be used to prosecute developers of legitimate software.
Important Note
The Computer Misuse Act has considerable crossover with the Data Protection Act 2018 and the General Data Protection Act (GDPR). These laws protect UK residents' personal data.
Under the Computer Misuse Act, the "material" accessed by a hacker does not need to be personal data. However, it commonly is. Records of credit card details, names and addresses, national insurance numbers, etc., can all be used for identity fraud.
The Data Protection Act and the GDPR place specific obligations on businesses to secure personal data against attackers. Failing to do so could lead to penalties and private legal claims.
Some means by which to achieve compliance with the Data Protection Act and the GDPR include:
- Maintaining a clear and comprehensive Privacy Policy
- Adhering to the GDPR's principles of data processing
- Implementing the concepts of data protection by design and by default
- Creating an IT Security Policy to ensure you meet the GDPR's security requirements
Offenses Under the Computer Misuse Act 1990

There are five criminal offenses listed in the Act. To make things simpler, we've numbered these offenses one to five, but they are more commonly referred to by the sections of the Act in which they appear.
Offense 1: Unauthorized Access to Computer Material
The first offense listed in the Computer Misuse Act is "unauthorized access to computer material," which amounts to "hacking." This offense occurs when a person knowingly uses a computer with an intent to obtain unauthorized access to any data or program stored on a computer. It covers remote or direct access, using the hacker's own computer or another computer.
Here's how the main part of this offense appears, at Section 1 of the Act:
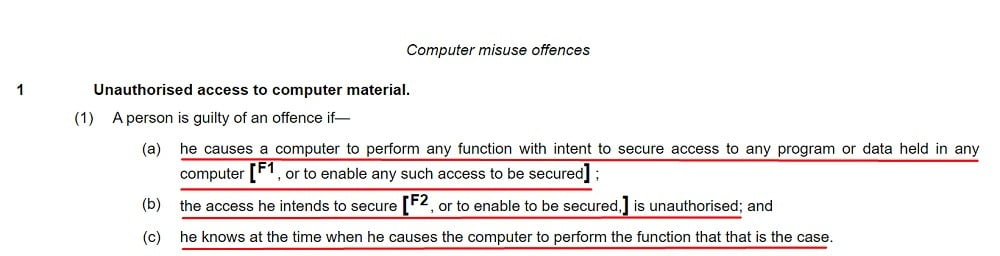
The hacker must be aware that their access is unauthorized (i.e. they cannot commit this offense accidentally).
The hacker must intend to access any unauthorized data or program, but this need not be any specific data or program. Therefore, speculative access (i.e. to see if anything valuable exists on a computer) is covered.
Important Note
A person can be guilty of the offense of "unauthorized access to computer material" if they have permission to access certain parts of a system but not others.
In the case of Regina v Bow Street ex p the U.S. Government, an employee who had some access to data on a computer was found guilty under the Act because he accessed information above his authority.
The court determined that "an employee should only be guilty of an offense if his employer has clearly defined the limits of the employee's authority to access a program or data."
Failing to clearly define the limits of your employees' access to data could leave you liable if they access unauthorized material.
Having a clear and robust IT Security Policy can help ensure your employees understand what data they can access and what data is off-limits.
Offense 2: Committing or Facilitating Further Offenses
The second offense under the Act is "unauthorized access with intent to commit or facilitate commission of further offenses." This offense occurs when a person accesses a computer with the intention of committing a crime or enabling another person to commit a crime.
Here's how the main part of this offense appears, at Section 2 of the Act:

Examples include where a hacker accesses a computer in order to divert money to their account or the account of another unauthorized person (the secondary crime being theft) or to obtain compromising material about another person (blackmail).
Offense 3: Intent to Impair the Operation of a Computer
The third offense under the Act is "unauthorized acts with intent to impair, or with recklessness as to impairing the operation of a computer." This offense occurs where a person, without authorization, does something in relation to a computer with the intention to:
- Prevent a computer from working properly
- Prevent access to a computer
- Prevent data or programs stored on a computer from working properly
A person can also be guilty of this offense if they:
- Enable another person to do the above things
- Do something reckless that might result in one of the above things
Here's how the main part of this offense appears, at Section 3 of the Act:

Cases prosecuted under this section may involve distributed denial of service (DDoS) attacks, where hackers flood a resource with web traffic in order to impair its functioning or prevent others from accessing it.
Offense 4: Unauthorized Acts Causing Serious Damage
The fourth offense under the Act is "unauthorized acts causing, or creating risk of, serious damage." This offense covers damage to critical infrastructure such as power grids, communications networks, transport systems, etc. Such activities are intended to cause widespread harm and could occur as part of a terrorist or cyber warfare attack.
This offense was added to the Act by a 2015 amendment.
Here's how the main part of this offense appears, at Section 3ZA of the Act:
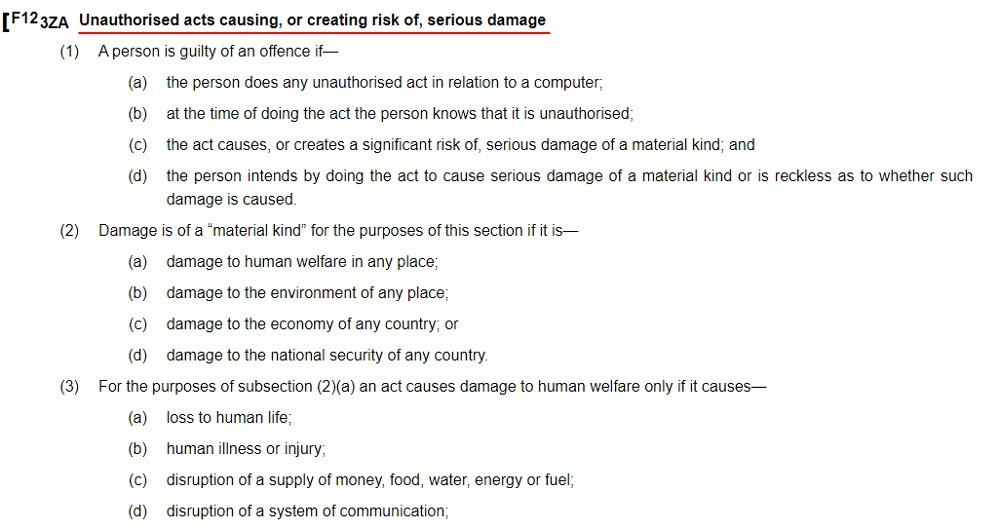
This can be a very serious offense, carrying the threat of life imprisonment in the most serious cases (more information about penalties is provided below).
Offense 5: Making, Supplying or Obtaining Articles for Use in Other Offenses
The fifth offense under the Act is "making, supplying or obtaining articles for use in an offense under Section 1, 3 or 3ZA" (what we've called "offenses 1, 3, and 4"). This offense covers the development, distribution, or obtaining of malware, password crackers, and other "hacker tools."
Such tools can be used by so-called "script kiddies," relatively inexperienced cybercriminals who use software created by others in order to obtain unauthorized access to, or cause damage to, a computer.
This offense was added to the Act by a 2006 amendment.
Here's how the main part of this offense appears, at Section 3ZA of the Act:

The "article" (program or data) must be "likely" to be used for hacking or other offenses. That is, the article doesn't need to have been developed in relation to a specific offense, but the developer must be shown to have believed that it would be used for such purposes.
Penalties for Violating the Computer Misuse Act 1990

All offenses listed in the Act, except offense four, are "either-way" offenses that could result in a "summary conviction" or an "indictment." Offense four is not triable "either way" and is only triable on indictment.
Whether a case is dealt with as a "summary trial" or a "trial on indictment" affects the maximum penalties available.
All criminal cases begin as "summary trials" at a magistrate's court, or, in Scotland, at a sheriff court with a single sheriff. Summary trials have lighter penalties, but they may be seen as less fair because they do not involve a jury.
A case may proceed to a "trial on indictment" if:
- The case is too complex for a summary trial, or
- The defendant requests trial-by-jury
Trials on indictment are heard at the Crown Court or, in Scotland, at a sheriff court (but with a jury). They can result in more serious penalties.
Penalties on Summary Conviction
For offenses one, two, three, and five, on summary conviction, the penalties can be:
- Imprisonment of up to 12 months (or imprisonment of up to six months in Northern Ireland)
- A fine of any amount (or a fine of up to £10,000 in Scotland)
- Both of the above
Offense four is not eligible for a summary conviction.
Penalties on Indictment
For offense one, "unauthorized access to computer material," the penalties on indictment are:
- Imprisonment of up to two years
- A fine of any amount
- Both of the above
For offense two, "unauthorized access with intent to commit or facilitate commission of further offenses," the penalties on indictment are:
- Imprisonment of up to five years
- A fine of any amount
- Both of the above
For offense three, "unauthorized acts with intent to impair, or with recklessness as to impairing the operation of a computer," the penalties on indictment are:
- Imprisonment of up to 10 years
- A fine of any amount
- Both of the above
For offense four, "unauthorized acts causing, or creating risk of, serious damage," the penalties on indictment are:
- Imprisonment of up to 14 years, or, in cases involving serious damage to human welfare or national security (or the risk thereof), possible life imprisonment
- A fine of any amount
- Both of the above
For offense five, "making, supplying or obtaining articles for use in an offense under Section 1, 3 or 3ZA," the penalties on indictment are:
- Imprisonment of up to two years
- A fine of any amount
- Both of the above
Summary
In this overview of the Computer Misuse Act 1990, we've looked at the five criminal offenses punishable under the Act:
- Unauthorized access to computer material
- Unauthorized access with intent to commit or facilitate commission of further offenses
- Unauthorized acts with intent to impair, or with recklessness as to impairing the operation of a computer
- Unauthorized acts causing, or creating risk of, serious damage
- Making, supplying or obtaining articles for use in an offense under Section 1, 3 or 3ZA
Defendants found guilty of any of these offenses can face fines and imprisonment.
To avoid falling victim to hackers, UK businesses should:
- Ensure they are compliant with the GDPR and Data Protection 2018
- Create an IT Security Policy that clearly defines staff access limits

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.




